Update: While this method still works, Apple now offers a more secure method called two-factor authentication.
Apple, like many other companies, offers increased security for your Apple account by way two-step verification.
Two-step verification is a simple and proven technique for stopping hacks that take advantage of stolen passwords and other sensitive information. As it is virtually impossible to bypass, it is worth your time to secure every important account that you have.
Taking five minutes to setup verification and add trusted devices to your account is much quicker (and cheaper) than spending a month disputing charges with your bank or credit card provider.
What is Two-Step Verification and Why is it Better?
As its name says, two-step verification requires a user to verify two different pieces of information before accessing an account.
Up until now, Apple occasionally used a weaker form of two-step verification when it noticed a change in your usage or location.
If you tried to purchase something on a different Wi-Fi network or had not logged in recently, they might ask questions like "What is your mother's maiden name?, "What was your first pet's name?", "Who was your favorite teacher?" and so forth.
While this form of two-step verification might slow down basic hackers, it doesn’t do much to protect you from someone who has your personal information.
The new two-step verification is different.
Instead of using existing personal information, the system generates a short PIN and sends it to your trusted devices. This means that unless the would-be hacker or identity thief has access to your individual recovery key or Apple’s databases, you can count on a higher level of security.
You can even assign multiple trusted devices to your account to ensure you can verify purchases with whatever iOS device you have nearby.
How Does Two-Step Verification Work?
When two-step verification is enabled, you start by logging in the same way you always have.
Instead of being granted immediate access, Apple will ask for a PIN which is then sent to you in a text message.
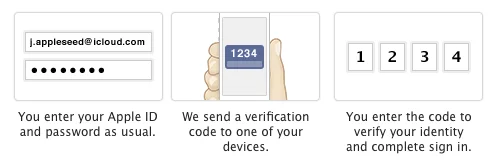 In effect, the PIN is a temporary single-use password.
In effect, the PIN is a temporary single-use password.
A bad guy can't look up a PIN sent only to your device or trick someone else into revealing it.
It is generated on-the-fly and right at the time you are logging in. It can be used only once! If it isn't used right away, it expires.
It's this ability to generate this temporary PIN and deliver it via a secure device that makes two-step verification so strong.
Instructions
-
1
Go to the Apple ID page at http://appleid.apple.com and click Manage your Apple ID.
-
2
Log into your account with your Apple ID and Password.
-
3
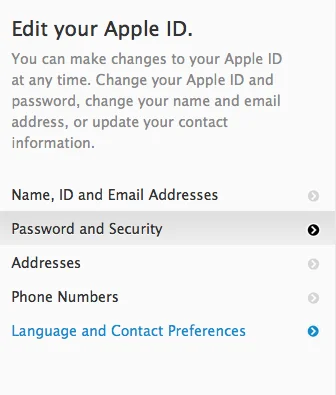
Select Password and Security in the left column. Click Continue to get to the "Manage your Security Settings" screen. This is the heart of it.
-
4
In the Two-Step Verification section, click Get Started. Don't worry about the other options on the page. Apple will present a couple of screens that explain how Two-step (sic) verification works.
-
5
If you do not see you device listed, clicking the Set up Find My iPhone link will add it to the list.

-
6
Verify Your Device
Once you’ve chosen a device, Apple will send a message containing a short four digit number. Enter it at the prompt and click Verify.
-
7
Put Your Recovery Key in a Safe Place
In the event your phone is broken, stolen or lost, a recovery key will allow you to access your account or set up two-step verification on your new device. This string of letters and numbers is important and shouldn’t be stored somewhere safe.
Don’t share it with anyone. Don’t store it in your email. Don’t store it on your phone or tablet.
-
8
Enable Two-Step Verification
All that’s left is to enter your recovery key at the prompt and click Enable Two-Step Verification.
The process is quick and easy. However, if you run into any problems, Apple has a full support page on the topic to help you out!
Tips & Warnings
- When your official "trusted device" is identified, Apple then gives you a Recovery Key and demands that you re-enter it to prove that you actually have it.
- You will need this Recovery Key only if you forget your password. You can give Apple the Recovery Key and you will be allowed to reset your password.
- If you sell or update your devices, be sure to head back to your account settings and update your Trusted Devices.
Video
Resources
Conclusion
Once two-step verification is in place, Apple will send your cell phone a code when you log in with you Apple ID and Password.
While you should still keep your Apple ID and password safe, this simple protection greatly reduces the chances of unauthorized access or purchases on your account.